Introduction
A Multilayer switch also known as a Layer 3 switch is a device that performs the function of a switch as well as a router also. The multilayer switch has the ability to operate at higher layers. It can perform both Layer 2 and layer 3 functions at extremely fast speed. This is also a great option for us if we want to perform InterVLAN routing. In a Multilayer Switch, the VLAN interface acts as a router interface having an IP address and a subnet mask. The configuration of a multilayer switch is very easy and simpler as compared to a Router-On-A-Stick(ROAS).Now take 2 PC's and a MultiLayer switch and connect it using a straight cable. Connect PC1 with interface fa 0/3 and PC2 with interface fa 0/5.
Now the first step is to vlan 3 and vlan 5 and assign vlan's to interfaces fa 0/3 and fa 0/5
switch(config)# vlan 3switch(config-vlan)# name vlan03
switch(config-vlan)# exit
switch(config)# vlan 5
switch(config-vlan)# name vlan05
switch(config-vlan)# exit
switch(config)# interface fa 0/3
switch(config-if)# switchport mode access
switch(config-if)# switchport access vlan 3
switch(config-if)# exit
switch(config)# interface fa 0/5
switch(config-if)# switchport mode access
switch(config-if)# switchport access vlan 5
Now after you have made access ports to interfaces, it's time to assign IP address to vlan 3 and vlan 5
switch(config)# interface vlan 3
switch(config-if)# ip address 192.168.3.1 255.255.255.0
switch(config-if)# exit
switch(config)# interface vlan 5
switch(config-if)# ip address 192.168.5.1 255.255.255.0
switch(config-if)# exit
The last command helps to perform routing in a multilayer switch. Without this command, the packets cannot be routed in a multilayer switch.
switch(config)# ip routing
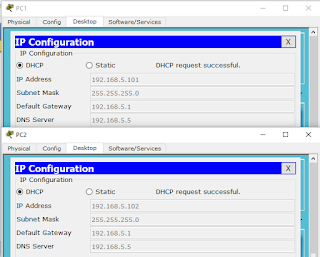
Now we assign IP adresses to PC1 and PC2 as shown below
Note that the default gateways of both the PC's contains the same IP address that we have given to VLAN interfaces. Now if we ping PC2 from PC1, we get the reply.